Panache Security Services
Panache Security Services has highly skilled staff with decades of experience in the security industry, along with systems developed over many years of engagement with both security companies and clients receiving a physical security service.
Panache Security Systems is dedicated to safeguarding businesses, retail stores, shopping malls, churches, housing estates and homes, factories and industrial parks, warehouses, power facilities, mines, commercial farms, schools and universities, government departments, and even concerts and large sporting events, by conducting in-depth, independent security audits. Our mission is to ensure that our clients receive the highest standard of security service, fostering a safe and secure environment at all times.
The SECURITY 5.0 COMPLIANCE AUDIT provides a comprehensive evaluation to assess the effectiveness of your current security measures and the services delivered by the security service provider.
Our highly experienced expert team focuses on ensuring that security service providers deliver security solutions that are marked by professionalism, transparency, and accountability, and who work with integrity and commitment to keep the client premises safe, are trustworthy, and are compliant with all applicable safety and regulatory standards.
Why Clients use Panache Security Services
Clients use Panache Security Services to ensure that they are receiving the physical security service that they are paying for, and which the security service provider company is contracted to deliver, as well as to correctly define the security measure and standards to ensure that clients best mitigate risk.
Questions clients should be asking themselves so as to determine if current security measures are truly providing the protecting needed:
- Are you receiving the security service you are paying for?
- Are you confident that your perimeter is TOTALLY SECURE?
- Have you had an INDEPENDENT SECURITY AUDIT conducted to ensure that you are adequately mitigating security risks?
- Does your Security Service Provider provide regular monthly management reports, including any security failures, along with corrective action taken?
- Is your organisation SECURITY 5.0 COMPLIANT?
If you are uncertain about, or answer ‘NO’ to any of these questions, you may be at risk. Our SECURITY 5.0 COMPLIANCE AUDIT is here to help you identify and address these gaps.
Take the Security Services Quiz
Your security is only as strong as its weakest link. In today’s ever-changing landscape of threats, ensuring that your property, assets, and people are protected requires more than just trust in your security service provider—it demands a thorough, objective assessment.
This quick and insightful quiz is designed to help you identify potential vulnerabilities and threats within your current security setup. By answering a few key questions, you’ll gain valuable insight into the effectiveness of your security measures and whether they truly meet the high standards required to safeguard your environment.
The results of this 20-question SECURITY SERVICES QUIZ can:
- Highlight critical gaps in your security that could leave you exposed.
- Offer a clearer picture of whether your security service provider is delivering the value you’re paying for.
- Empower you to take proactive steps toward achieving SECURITY 5.0 COMPLIANCE.
Take the quiz now and discover how secure your operations really are — because your safety and peace of mind deserve nothing less than excellence.
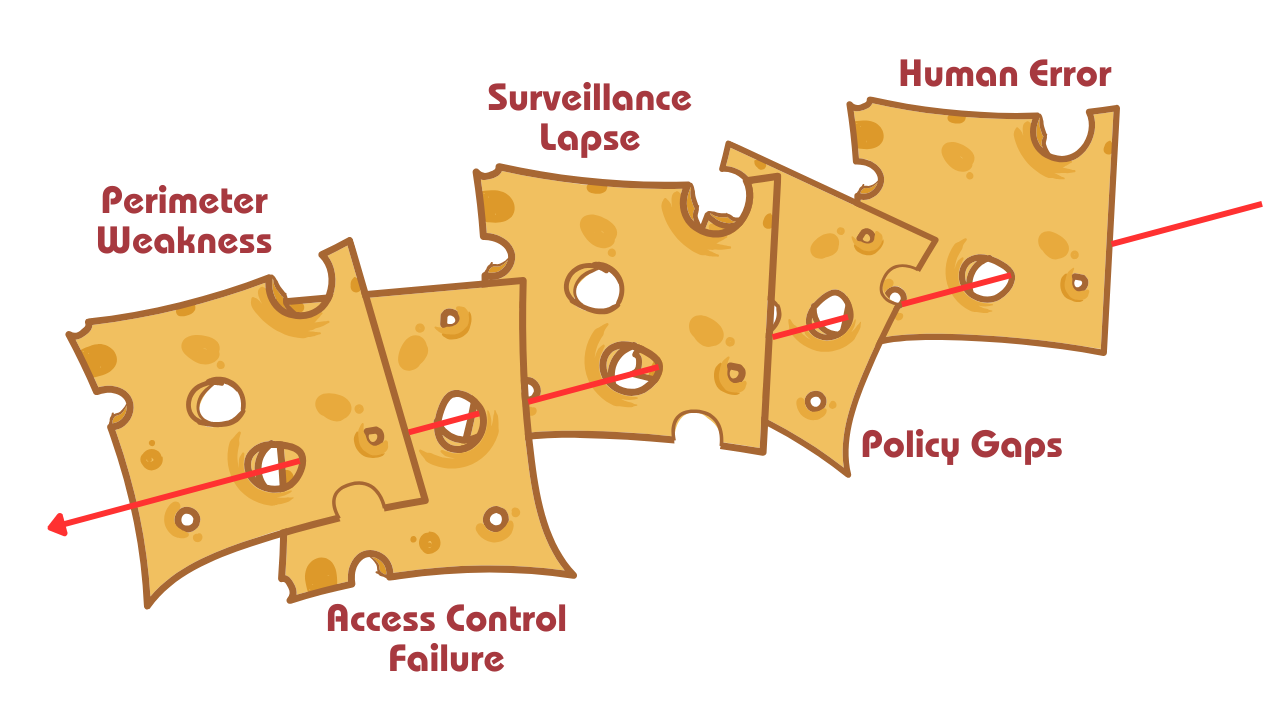
Alignment of Security Failures
Very seldom is a security breach the result of a single factor. More often than not it is a combination of a number of security failures, which combine to allow the security breach.
Swiss Cheese Model
The Swiss Cheese Model, developed by James Reason, is a powerful framework for understanding how multiple failures can align to result in a security breach. In physical security, this model can illustrate how various layers of defense, each with their own vulnerabilities, more often than not fail simultaneously for a breach to occur.
Layers of Defense
Imagine your security measures as slices of Swiss cheese stacked on top of each other. Each slice represents a layer of defense, such as:
- Perimeter Security (fences, walls, and gates)
- Access Control Systems (badges, biometrics, and locks)
- Surveillance (CCTV cameras and monitoring personnel)
- Guard Patrols and Response Teams
- Security Policies and Protocols
Ideally, these layers should work together to prevent unauthorised access. However, like Swiss cheese, no layer is perfect—each has holes or weaknesses.
Alignment of Failures
A breach most occurs when the holes in multiple layers align, creating a direct path for the threat. For example:
- Perimeter Weakness: A damaged fence or unlocked gate allows unauthorised entry.
- Access Control Failure: A staff member shares their access badge or password.
- Surveillance Lapse: Cameras are poorly positioned or not monitored.
- Human Error: Guards fail to follow protocols during an incident.
- Policy Gaps: Security measures are outdated or poorly enforced.
Each individual failure may seem minor, but when they align, they can create an opportunity for a breach.
Application of the Swiss Cheese in Security Audits
The Swiss Cheese Model underscores the importance of:
- Layering Security Measures: Ensuring no single failure compromises the system.
- Identifying Vulnerabilities: Regular audits to find and address “holes” in each layer.
- Integrating Systems and Training: Coordinating technology, personnel, and policies to minimise alignment of failures.
By adopting a proactive approach and addressing weak points in each layer, organisations can significantly reduce the likelihood of breaches. The SECURITY 5.0 COMPLIANCE AUDIT is designed to identify and plug these gaps before they align to create a security failure.
Which brings us to the world-leading SECURITY 5.0 COMPLIANCE AUDIT, along with other security products and services . . . all working to ensure that holes in the Swiss cheese don’t align in your business!
Products & Services
Panache Security Services specialises in offering advanced services to clients who employ the services of a security service provider.
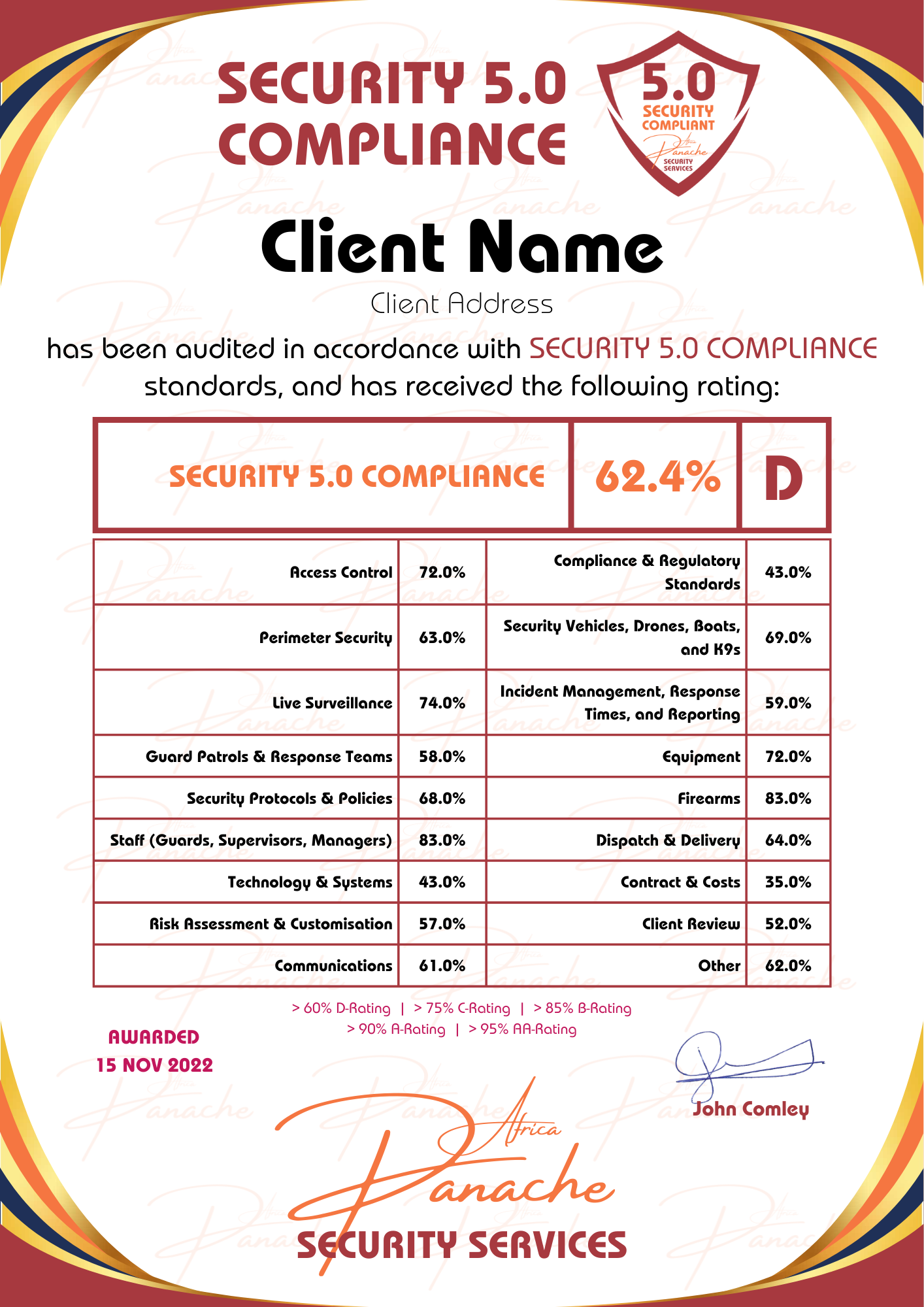
SECURITY 5.0 COMPLIANCE AUDIT
Our SECURITY 5.0 COMPLIANCE AUDIT is designed to give you peace of mind by ensuring your security service provider meets industry standards and protects your assets effectively. This audit provides an objective review of all security measures on your premises, identifying potential vulnerabilities, and assessing whether you are receiving the security service you deserve.
AUDIT SCOPE
Over and above an overall review of the Security Contract and the Costs of the Security Service provided, conducting a SECURITY 5.0 COMPLIANCE AUDIT is about auditing the Property and Buildings, the Security Staff Employed, the Tools & Technology Deployed, the Guarding Rules and Guidelines, the Management Guidelines, and the Systems & Processes implemented and followed. Thereafter, what follows is the issuance of a SECURITY 5.0 COMPLIANCE AUDIT report, requiring corrective action in areas scoring below 75%, which is then followed by a final inspection to ensure that recommendations have been adequately implemented, following which a SECURITY 5.0 COMPLIANCE CERTIFICATE will be issued, based on the final results.
Furthermore the SECURITY 5.0 COMPLIANCE AUDIT will provide an analysis of the current costs of the security service, including recommendations on possible areas for cost saving.
INDUSTRIES SERVICED
The SECURITY 5.0 COMPLIANCE AUDIT is specific to the following industries:
- Businesses,
- Retail Stores
- Shopping Malls
- Churches
- Housing Estates & Homes
- Factories and Industrial Parks
- Warehouses,
- Power Facilities
- Mines
- Commercial Farms
- Schools and Universities
- Government Departments
- Concerts and Large Sporting Events
As well as any other industry or environment where a physical security service is used.
AUDIT KEY FOCUS AREAS
The key areas of the SECURITY 5.0 COMPLIANCE AUDIT include:
-
- Access Control – Evaluates secure entry points, visitor screening, and access credential management.
- Perimeter Security – Assesses fences, barriers, lighting, and deterrents to prevent unauthorised entry.
- Live Surveillance – Reviews in-the-field surveillance as well as real-time monitoring systems, including cameras and control rooms, for situational awareness.
- Guard Patrols & Response Teams – Examines patrol effectiveness, emergency response readiness, and incident handling.
- Security Protocols & Policies – Ensures documented procedures align with best practices and client requirements.
- Staff (Guards, Supervisors, Managers) – Evaluates training, qualifications, and overall staff competency in security roles.
- Technology & Systems – Reviews advanced security tech, including CCTV, alarms, sensors, and integrated systems.
- Risk Assessment & Customisation – Identifies site-specific vulnerabilities and provides tailored security strategies.
- Communications – Audits communication tools and processes for quick, effective incident reporting.
- Compliance & Regulatory Standards – Confirms adherence to industry regulations and applicable local security laws.
- Security Vehicles, Drones, Boats, and K9s – Evaluates deployment of specialised equipment, tools and resources for enhanced protection.
- Incident Management, Response Times, and Reporting – Reviews efficiency in detecting, responding to, and documenting incidents.
- Equipment – Assesses the quality, functionality, and maintenance of essential security gear.
- Firearms – Evaluates firearm licensing, storage, training, and compliance with legal standards.
- Dispatch & Delivery – Reviews the coordination and timeliness of security service deployment.
- Contract & Costs – Ensures transparency, value for money, and alignment with service expectations.
- Client Review – Collects client feedback on service satisfaction, concerns, and improvement opportunities.
Our audit endeavours to ensure that your security service provider acts in your best interests, upholds high standards of training, promotes occupational safety, and ensures regulatory compliance.
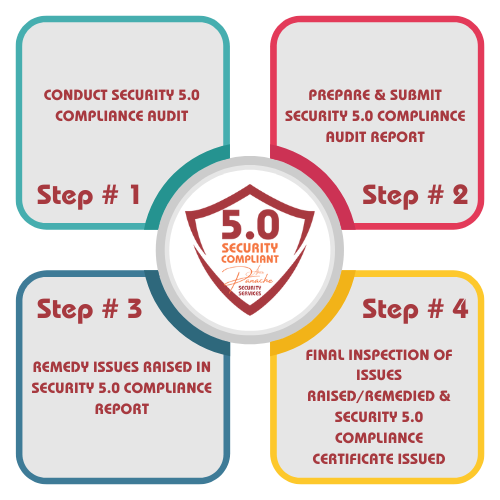
4-Step Process for SECURITY 5.0 COMPLIANCE AUDIT
The SECURITY 5.0 COMPLIANCE AUDIT follows a 4-Step Process.
STEP # 1
CONDUCT SECURITY 5.0 COMPLIANCE AUDIT
- Commence with SECURITY 5.0 COMPLIANCE AUDIT
- Meet with Client and Security Service Provider Management
- Conduct Onsite Interviews and Inspections
STEP # 2
PREPARE & SUBMIT SECURITY 5.0 COMPLIANCE AUDIT REPORT
- Prepare SECURITY 5.0 COMPLIANCE AUDIT report
- Present SECURITY 5.0 COMPLIANCE AUDIT report to Client and Security Service Provider
- Review Issues Raised & Remedial Action
STEP # 3
REMEDY ISSUES RAISED IN SECURITY 5.0 COMPLIANCE REPORT
- Security Service Provider remedies issues raised in the SECURITY 5.0 COMPLIANCE AUDIT report
STEP # 4
FINAL INSPECTION OF ISSUES RAISED/REMEDIED & SECURITY 5.0 COMPLIANCE CERTIFICATE ISSUED
- Conduct final inspection of issues raised in the SECURITY 5.0 COMPLIANCE AUDIT report
- Issue SECURITY 5.0 COMPLIANCE CERTIFICATE
SECURITY SERVICE & TECHNOLOGY RECOMMENDATIONS
Our SECURITY SERVICE & TECHNOLOGY RECOMMENDATIONS service is a proactive service, providing clients with a report on the type and level of security service needed, along with the security technology recommended to mitigate security risks, BEFORE engaging with or committing to a security service or technology purchase and deployment. This service is designed to give you peace of mind by offering:
- An analysis of security threats and risks
- Recommended type and level of security service needed to mitigate the threats and risks identified
- Recommended type of security technology and equipment needed to mitigate the threats and risks identified
- Recommended costs for both security services
- Recommended costs for security technology and equipment
- Security service contract template
Panache Security Services have experts in all areas of security along with technologies commonly deployed, and are able to offer unfettered advice on what is best for your environment, thereby providing you with the best technology to fit your budget.
NOTE: Panache Security Service has no affiliations to any security service providers or security technology and equipment providers, so are able to offer clients completely unbiased opinions.
What Our Clients Say About Us . . .
Residential Estate
“The SECURITY 5.0 COMPLIANCE AUDIT by Panache Security Services was invaluable for our housing estate. They assessed every aspect of our security, from access points to resident safety protocols, giving us a clear roadmap for improvement. We’ve since upgraded our systems, and the peace of mind it brings to our residents is priceless.”
– Residential Estate Security Supervisor
Shopping Mall
“Panache Security Services’ SECURITY 5.0 COMPLIANCE AUDIT helped us take a fresh look at our security protocols. Their expertise and attention to detail uncovered risks we were unaware of, and their solutions were tailor-made for our high-traffic environment. Our mall feels safer, and our customers have noticed the difference.”
– Shopping Mall Security Manager
Manufacturing Facility
“Panache Security Services’ SECURITY 5.0 COMPLIANCE AUDIT brought an objective view to our facility’s security needs. They identified weak points in our personnel access control and provided solutions that were easy to implement. Our security has tightened considerably since the audit, and it’s had a positive impact on operations.”
– Manufacturing Facility Operations Director
Warehouse
“Our SECURITY 5.0 COMPLIANCE AUDIT with Panache Security Services was a game-changer. They uncovered vulnerabilities in our inventory tracking and loading bay security that we hadn’t anticipated. Thanks to their guidance, we’ve significantly reduced theft and enhanced the security of high-value goods.”
– Warehouse Security Coordinator
Mine
“The SECURITY 5.0 COMPLIANCE AUDIT conducted by Panache Security Services was essential for our high-risk mining site. They identified specific improvements in our perimeter controls and emergency protocols. Since implementing their recommendations, our site security has improved dramatically, and our workforce feels more protected.”
– Mine Safety and Security Supervisor
Housing Estate
“Panache Security Services conducted a SECURITY 5.0 COMPLIANCE AUDIT for our estate, and the results have been impressive. Their team identified gaps in our perimeter security and entry protocols, which we were able to address immediately. Residents now feel safer, and we’ve already seen a decrease in unauthorised entries. Highly recommend their professional service!”
– Housing Estate Security Coordinator
Community Association
“Working with Panache Security Services on a SECURITY 5.0 COMPLIANCE AUDIT was eye-opening. Their audit identified security issues we hadn’t considered, including nighttime perimeter monitoring and visitor tracking. Since making the changes, our residents have reported feeling much more secure. Excellent service!”
– Community Association Chairperson
Power Generation Facility
“Panache Security Services conducted a SECURITY 5.0 COMPLIANCE AUDIT that provided us with an in-depth evaluation of our facility. Their audit gave us actionable insights that have boosted our security measures across the board. It’s clear they understand the unique needs of critical infrastructure.”
– Power Generation Facility Risk Manager
Retail Store
“Panache Security Services conducted a comprehensive SECURITY 5.0 COMPLIANCE AUDIT for our store, revealing vulnerabilities we hadn’t considered. Their recommendations were clear and practical, and since implementing them, we’ve seen a significant improvement in security and customer peace of mind. An invaluable service for any retail business!”
– Retail Store Security Director
* In accordance with POPI and client NDA agreements, all testimonials are redacted to exclude names and locations
Other Services . . .
FORENSIC AUDITING
A FORENSIC AUDIT aims to uncover financial misconduct by combining investigative techniques, auditing procedures, and a deep understanding of legal standards. The findings are often used to support legal action or remedial measures, so the accuracy and thoroughness of the process are critical.
Panache Security Services partners with multiple financial auditing firms, and which provide comprehensive forensic audits.
CYBERSECURITY AUDITING
A CYBERSECURITY AUDIT assesses an organisation’s digital infrastructure to identify vulnerabilities, evaluate compliance with security standards, and recommend solutions to mitigate risks. These audits, which include ‘penetration testing’, are critical in safeguarding sensitive information and preventing cyberattacks, ensuring that systems are robust and secure.
Panache Security Services collaborates with leading cybersecurity experts to provide thorough and reliable cybersecurity audits.
INVESTIGATIONS
Panache Security Services has a highly-skilled team, capable of carrying out complicated INVESTIGATIONS.

ARE YOU SURE YOU ARE RECEIVING THE SECURITY SERVICE YOU ARE PAYING FOR?
Your security is only as strong as its weakest link. In today’s ever-changing landscape of threats, ensuring that your property, assets, and people are protected requires more than just trust in your security service provider—it demands a thorough, objective assessment.
This quick and insightful quiz is designed to help you identify potential vulnerabilities and threats within your current security setup. By answering a few key questions, you’ll gain valuable insight into the effectiveness of your security measures and whether they truly meet the high standards required to safeguard your environment.
The results of this 20-question SECURITY SERVICES QUIZ can:
- Highlight critical gaps in your security that could leave you exposed.
- Offer a clearer picture of whether your security service provider is delivering the value you’re paying for.
- Empower you to take proactive steps toward achieving SECURITY 5.0 COMPLIANCE.
Take the quiz now and discover how secure your operations really are—because your safety and peace of mind deserve nothing less than excellence.
Contact Us TODAY!
Contact us TODAY to find out more about the security services offered by Panache Security Services!
Terms of Service Privacy Policy Contact Us Copyright © 2025 Panache Africa Group Website Development & Maintenance by Panache Business Consulting Services